 Last year’s high profile attack on home broadband routers brought into focus a problem that’s been brewing for many years: the lax security of a crucial bit of hardware we all rely on.
Last year’s high profile attack on home broadband routers brought into focus a problem that’s been brewing for many years: the lax security of a crucial bit of hardware we all rely on.
Broadband routers are not just a gateway to the internet, they’re also the gatekeepers which are supposed to help protect our devices. But many routers are insecure and vulnerable to attack.
Sometimes this is due to unpatched flaws in the hardware’s operating system. But there’s also a gap in the knowledge of many home broadband users when it comes to configuring a router, and many of us do not take basic precautions which could improve security.
We recently surveyed 2,000 visitors to our site to find out more about how much Britain’s broadband users knew about their routers and what steps they’d taken to secure their network.
54% of those surveyed said they were “very concerned” or “somewhat concerned” about the possibility of their router being attacked, so there is at least a reasonable awareness of the risks. However, it’s worrying to discover that a fairly low percentage had taken basic precautions or even knew how to - 53% of respondents had not changed their Wi-Fi or router admin password. Few have even accessed their router’s administrator controls.
But while it’s important to have at least some rudimentary knowledge, ISPs should also be doing their bit, patching flaws when they're discovered and offering sufficient help to guide their customers. This is vitally important when our survey found that 86% use the ISP issued router.
Read on below for more detailed results from our survey. And if you’d like to find out how to safeguard your broadband, read our beginner's guide to router security.
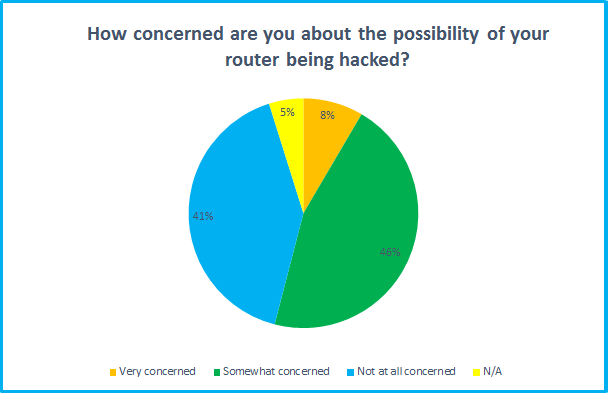
While 53% are concerned about the dangers of a router hack, that still leaves 47% who aren't too worried. Some may be confident because they've taken precautions, but others may simply be unaware of the risks.
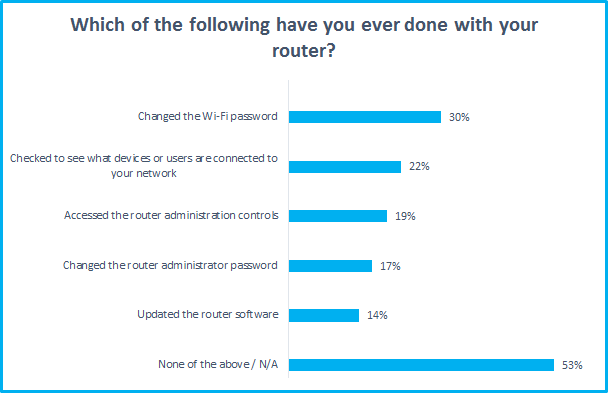
It is concerning that so many broadband users have apparently never touched their router's security settings, not even accessing the admin controls. This suggests that many millions of routers are running with default passwords and settings.
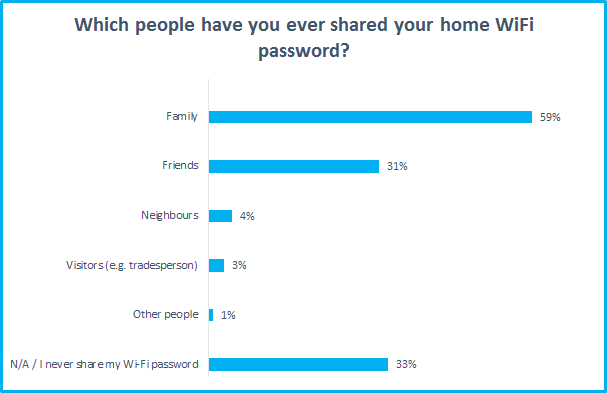
Think before giving out your Wi-Fi password. Once connected, Wi-Fi users may be able to view shared drives and access connected devices, and anything they do on your broadband would be traced back to the bill payer. We would hope family and friends can be trusted, but sharing with neighbours may not be the best idea unless you're on very good terms. Some routers offer a guest network feature which restricts access, so use this if you want to grant Wi-Fi access and protect your privacy.
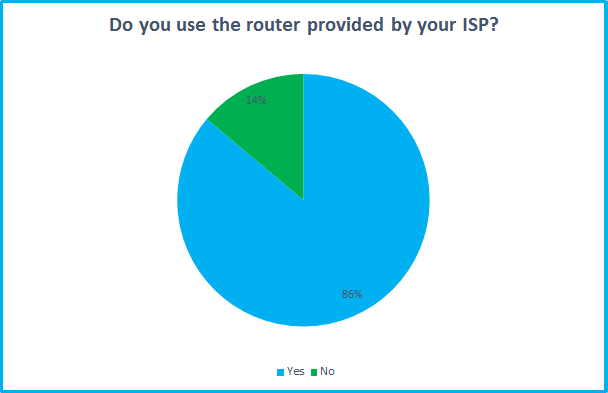
It's not surprising to discover most people use the ISP supplied router. After all, these are often free. But it's important to update the default settings and watch out for software updates. Buying your own router may be preferable if you want more security and extra features.
Interview with Ondrej Vlcek, CTO of Avast Software
To find out more about the issue of router security, we spoke with Ondrej Vlcek, Chief Technology Officer for leading anti-virus firm Avast.
Broadband Genie: How important is it to update router firmware and change the wifi and administration passwords?
Ondrej Vlcek: What many people are unaware of is that their router is the core entry point to their connected home and all their connected devices. Each Internet-connected device, whether it be a laptop, mobile phone, security camera or TV, connects to the Internet and their local network via a router. All exposure to threats in the home must come through the router which remains the weakest link in the security is essentially the gatekeeper to the home network. If the router is weakened by a vulnerability, attackers can enter the home network and strike other potentially vulnerable devices connected to it such as iPads and refrigerators.
Home routers are weak and, therefore, also vulnerable, because for the most part, Internet service providers, router manufacturers and the security community have neglected to acknowledge, scrutinize, and address their weaknesses. Over the last few months, Avast scanned over 4.3 million routers around the world and found that 48% have some sort of security vulnerability. Today’s router security situation reminds me of the security of PCs in the 1990s, with simple vulnerabilities being discovered every day.
BBG: Are there any hacks or possible security threats that routers are particularly vulnerable to?
OV: If the router is compromised, the entire home network and all devices on it can be compromised as well. Attackers can take advantage of routers to do many malicious things, which includes the following:
1. DNS hijacking – attackers decide what pages are visited. Domain name service (DNS) is a service developed to help people so they don’t have to memorize IP addresses used by computers to communicate with each other over a network. When a user enters google.com into an address bar, the computer asks a specific DNS server to translate the name to an address. The DNS server address is usually provided automatically by the user’s Internet provider, but it can be changed manually. If an attacker has access to the router, they can change the provider’s (legitimate) DNS server to their own (malicious) DNS server. If users enter login credentials to such a spoofed page, they give their credentials directly to the attacker.
2. Botnets – turning routers into a soldiers to attack others. Many routers have some kind of remote access turned on by default. If the user doesn’t change the default passwords and allows remote access services to be accessible from the Internet, they become a gate secured by a chain with a knot. Anyone can open it. Once the attacker guesses the correct username and password combination (which is extremely easy, considering default passwords are available all over the Internet), they can install almost any program to the router. If the program of choice happens to be a malicious bot, the router becomes part of the botnet and can be used to run distributed denial of service attacks (DDoS), send spam or attack other routers on the Internet.
3. Traffic monitoring tools – the ultimate spy gadget. If an attacker can install traffic monitoring tools, such as tcpdump, to your router, they can read all the unencrypted communication that travels through the router.
4. Proxy – an invisibility cloak for attackers. The attacker doesn’t have to install anything. The most common ways to remotely access a router are through the use of a Secure Shell (SSH) server, which, if available, can be used as a disguise for the attacker. This means that if the attacker decides to attack somebody on the Internet, the address will be visible is not that of the attacker, but that of a compromised router.
5. Weak passwords - wi-Fi routers can use several types of encryption methods, ranging from no encryption at all (unsafe, open networks) to enterprise and complex WPA2 encryption with authentication servers. Not using any encryption methods or using weak (WEP, WPA) encryption is not recommended, as it can be easily cracked, and even though the personal WPA2 encryption provides better security it is still not very safe if used with weak passwords. An eight-digit number password can be cracked within a few minutes.
BBG: How often should users look to replace their current router?
OV: If people take action to secure their router by changing the password on a regular basis to prevent attacks, then a router can last without needing to be changed too often.
BBG: Do you have any top tips for users to follow to help secure their router?
OV: People should think twice about the password they use for their Wi-Fi network. Combining letters, numbers and special characters is highly recommended for better protection. Creating a long passphrase instead of a password is also recommended. It is important to remember that once an attacker is able to connect their device to a router, they are on the same network and can reach other devices.
Additionally, if a weak (or even default) password is used for the administrative interface of the router, the router – and all the devices connected to it -become completely vulnerable to all kinds of attacks from the Internet, even if the router’s administrative interface itself isn’t open to the Internet. This is a relatively little-known fact, even among the security experts.